Your smart phone can't recognize who you are, although your security keeps improving. You always carry it with your passwords, don't you? It may be a part of your body. You can't lose it.
None dualistic duality is well known idea about quantum computers. 0 and 1 are treated at the same time.
Absurdity and irrationality are quite natural in Zen.
Birds can't perceive their own chicks. A cuckoo puts her eggs in the nest of different birds.
Her egg is in 0, and 0 is replaced to 1.
There are 3 independent hashings, (0,6,7) in the nest. Θ(1) survive, although 0 is the cuckoo. Θ(log logU) is the collision, which is 1.58.
U={0,1,・・・,U-1}
This is the hash table. You will expand it to create empty space for k independence.
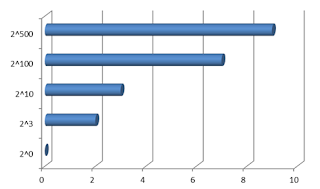
When U=2^100, there are only 6.64 collisions. Therefore, the wider space must be better.